Years before James Boulware was killed by a SWAT Sniper’s bullet, he was arrested in 2013 for choking a family member and threatening to go on a shooting spree. According to Dallas County court records, the case was dismissed in April 2014 after Boulware met court-ordered conditions.
Years later, he would lay explosive devices and open fire on a Dallas Police Headquarters Building, thus completing his path path toward intended violence.
Could this tragedy have been prevented?
In a word, Yes.
Effective threat assessment is about a totality of circumstance. This means the focus should be more on the concerning patterns of behavior that occur over the course of space and time rather than the assessment of a specific incident in the context of a singular occurrence. As history has shown, targeted violence is the result of an identifiable and observable process of thinking and behavior that when identified, assessed, and managed has been proven to prevent violent outcome.
In their book, “Threat Assessment and Management Strategies” Frederick S. Calhousn and Stephen W. Weston discuss the observable behaviors threat assessors need keep in mindful when assessing any inappropriate communication.
Attack-related behaviors are best conceptualized as steps hunters must take to carry out acts of premeditated violence. We call this concept the path to intended violence. Essentially, the stepping stones consist of:
“Grievance, which is the motive or reason compelling the hunter to act.”
After losing custody of his son, “He [James] said, ‘Dad, I have lost my house, my tools, my son. I’m going through every dime I’ve got. I can’t find a job because I got domestic violence on my record.’ He said, ‘I’ve lost everything.’ ” (Source)
“Ideation, which requires actually settling upon the idea that violence is justified and necessary.”
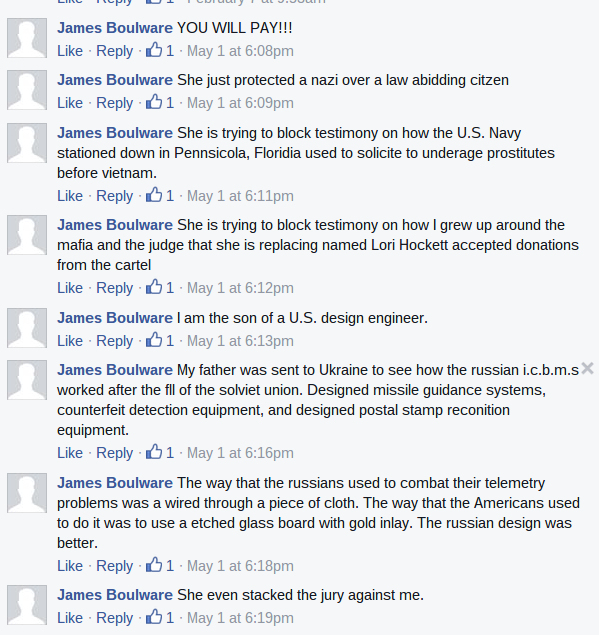
James Boulware made repeated facebook postings expressing his grievance, and on the page of the judge who presided his case, he also regularly commented on the website Disqus:
“Research and planning, which means going beyond the idea to actually figuring out how to consummate the violence.”
On the pathway to violence, those who wish to do harm must first engage in some form of research and planning to determine the likelihood of success for their intended action.
A key component to to bringing a threat assessment case toward peaceful resolve is identifying the subject’s attack-related behavior. These are the self-identifying patterns on the pathway to violence that include research, planning, weapon acquisition, training, and logistical considerations. The research and planning phase provides the best protective intelligence to determine if the subject poses a realistic threat that is likely to escalate into violence. This phase also offers the most observable monitoring of the time, money, and effort, being invested in the subjects willingness to do harm. This phase is crucial in determining if the offender will continue on the path toward violence or if they will transfer their ideation toward a more easily accessible target.
The Judge said she had been threatened multiple times by Boulware since the custody trial and had increased her security as a result. Unable to successfully get to the judge, It’s likely this made police headquarters a much easier target to successfully attack.
“Preparation, which involves obtaining the necessary equipment, such as weapon of choice, and taking any other actions required to initiate the plan.”
The research and investment required to purchase a ‘ZOMBIE APOCALYPSE ASSAULT VEHICLE AND TROOP TRANSPORT’ was a clear indicator that James Boulware was escalating in his intent to harm.
This is also the stage of events where James Boulware would have acquired the materials to build and test his explosive devices.
“Breach, which entails initiating the plan by circumventing the target’s security (however primitive or sophisticated that may be) to launch the attack.”
The breach phase is final opportunity for protective elements to stop the imminent attack. As in Boston, when the terror suspect presented the knife before lunging at federal agents there is precious little time to recognize and de-escalate the threat.
Without an effective threat assessment team or protective intelligence assets to assess and monitor the self-identifying behaviors James Boulware displayed, the only opportunity left to the police to thwart the attack on their headquarters came when Mr. Boulware left the protection of his armored van to emplace the explosive devices around the police headquarters building.
“Attack, which is the actual physical assault. “
At 12:30am on Saturday, June 13th, 2015, gunfire is reported outside the Dallas Police Department’s headquarters.
For far too long, over-arching security measures have done nothing more than vacillate between hyper-vigilance and complacency. Safety lies in the middle – a byproduct of awareness and preparation. Protective Intelligence is the process for collecting and assessing information about persons who have interest, motivation, intention, and practical capability to due harm. Rather than promote the invasive efforts of big-brother intrusion, protective intelligence affords a way to effectively monitor self-identifying activity and then manage those potentially violent outcomes toward peaceful resolve.
We as a society can no longer afford to operate in a world where we simply hope that nothing will happen, and then solely rely on the response of others to save us once something does. Doing nothing is a choice. Today’s protective posture require a preventative approach to safety, and the best preventative policy begins with an effective protective intelligence program.
———————————————————
Spencer Coursen is a nationally recognized threat management expert who has an exceptional record of success in the assessment, management, and resolution of threats, domestic and global security operations, investigations, policy authorship, and protective strategy.